As a follow-up of one of Claudia Beisiegel’s WebSphere and Cloud Pak for Apps Customer Advisory Board (CAB) sessions I read the article SAML assertions across WebSphere Application Server security domains again which reminded me that I’ve documented the required steps how to use SAML group configurations for role assignments in tWAS some time ago. As these steps are not really intuitive (at least for me) I thought it might be useful for others as well.
Configuration of SAML group mappings in tWAS
To use group information from the SAML Token for role assignment in WebSphere Application Server applications you need to create a trusted realm in WebSphere Application Server and then specify the proper realm name when assigning groups to the role in WebSphere application server.
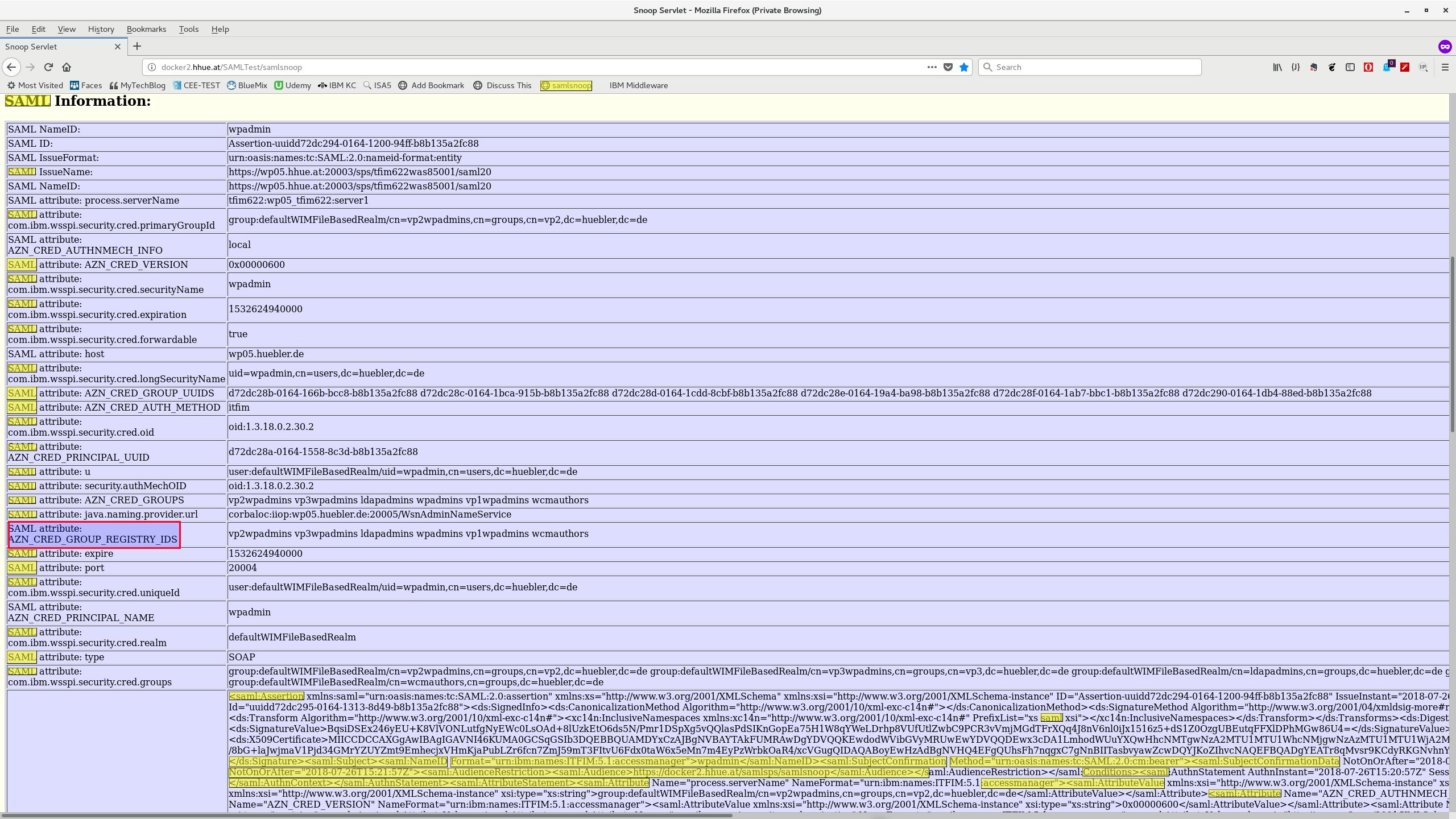
The attached file Snoop_Servlet.pdf contains the full SAML Token based on which we determined the sso_<id>.sp.groupName attribute which is marked in the screenshot here:
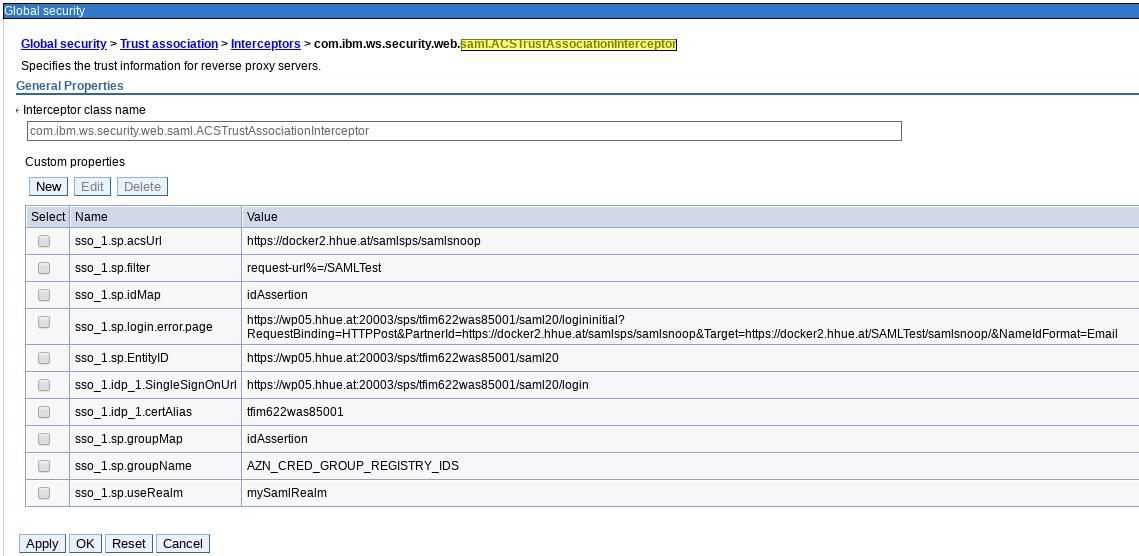
The WAS Saml configuration looks like the following (you might optionally configure a realm name here as well). The default realm name being used is the IssuerName which is the IdPs sso_<id>.sp.EntityID property (some docs say: sso_<id>.idp_<id>.EntityID). See the WebSphere Information Center for details on sso<id>.sp.defaultRealm_ and sso_<id>.sp.useRealm):
The WAS Saml configuration with a custom realm name defined being used here is the following:
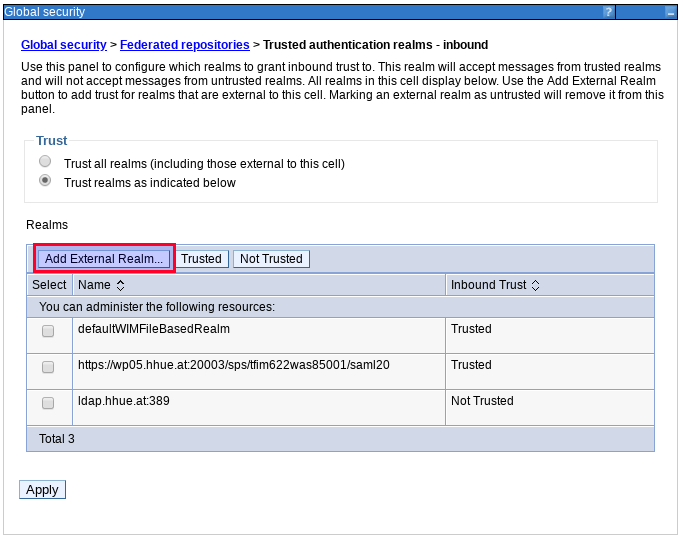
As the SAML Realm is not in WebSphere we need to define an External Realm which we trust in WebSphere Application Server:
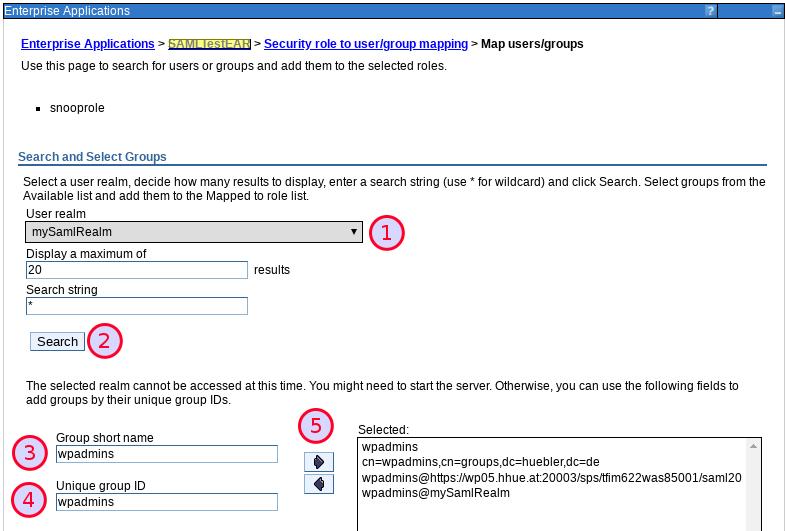
Next we need to assign a group to the role definition in the application. Here we can now select the Realm from the DropDown box and we need to enter the group name:
Debugging
For the testing and debugging we used the following trace string: *=info: com.ibm.ws.security.*=all: com.ibm.websphere.security.*=all: com.ibm.websphere.wim.*=all: com.ibm.wsspi.*=all: com.ibm.ws.wim.*=all
And the relevant section in the trace is the following:
[7/26/18 15:40:51:721 UTC] 000000bf WSAccessManag < isSpecialSubjectGrantedAnyRole Exit
false
[7/26/18 15:40:51:721 UTC] 000000bf WSAccessManag > isGrantedAnyRole Entry
Authorization Table [ com.ibm.ejs.models.base.bindings.applicationbnd.impl.AuthorizationTableImpl@90127803 ]
Authorization Table contains [ 1 ] role assignments
Role Assignment [ com.ibm.ejs.models.base.bindings.applicationbnd.impl.ApplicationbndFactoryImpl$1@f75b4328 ]
Security Role [ org.eclipse.jst.j2ee.common.internal.impl.SecurityRoleImpl@f11c8c4b ]
Role Name [ snooprole ]
Role Assignment contains [ 0 ] users
Role Assignment contains [ 4 ] groups
Subject [ com.ibm.ejs.models.base.bindings.applicationbnd.impl.GroupImpl@3e1c5429 ]
Name [ wpadmins ]
Access ID [ group:defaultwimfilebasedrealm/cn=wpadmins,cn=groups,dc=huebler,dc=de ]
Subject [ com.ibm.ejs.models.base.bindings.applicationbnd.impl.GroupImpl@98be0797 ]
Name [ cn=wpadmins,cn=groups,dc=huebler,dc=de ]
Access ID [ group:ldap.hhue.at:389/cn=wpadmins,cn=groups,dc=huebler,dc=de ]
Subject [ com.ibm.ejs.models.base.bindings.applicationbnd.impl.GroupImpl@174ee99b ]
Name [ wpadmins@https://wp05.hhue.at:20003/sps/tfim622was85001/saml20 ]
Access ID [ group:https://wp05.hhue.at:20003/sps/tfim622was85001/saml20/wpadmins ]
Subject [ com.ibm.ejs.models.base.bindings.applicationbnd.impl.GroupImpl@e42c9d11 ]
Name [ wpadmins@mySamlRealm ]
Access ID [ group:mysamlrealm/wpadmins ]
Role Assignment contains [ 0 ] special subjects
[Lorg.eclipse.jst.j2ee.common.SecurityRole;@17b89324
com.ibm.ws.security.auth.WSCredentialImpl@52e2b929
[7/26/18 15:40:51:721 UTC] 000000bf WSAccessManag > getAccessId Entry
[7/26/18 15:40:51:721 UTC] 000000bf WSCredentialI > getAccessId Entry
[7/26/18 15:40:51:721 UTC] 000000bf WSCredentialI < getAccessId Exit
user:mySamlRealm/wpadmin
[7/26/18 15:40:51:721 UTC] 000000bf WSAccessManag < getAccessId Exit
user:mysamlrealm/wpadmin
[7/26/18 15:40:51:721 UTC] 000000bf WSAccessManag > getGroupsIds Entry
com.ibm.ws.security.auth.WSCredentialImpl@52e2b929
[7/26/18 15:40:51:721 UTC] 000000bf WSCredentialI > getGroupIds Entry
[7/26/18 15:40:51:721 UTC] 000000bf WSCredentialI < getGroupIds Exit
[group:mySamlRealm/vp1wpadmins, group:mySamlRealm/wpadmins, group:mySamlRealm/wcmauthors, group:mySamlRealm/ldapadmins, group:mySamlRealm/vp3wpadmins, group:mySamlRealm/vp2wpadmins]
[7/26/18 15:40:51:721 UTC] 000000bf WSAccessManag < getGroupsIds Exit
group:mysamlrealm/vp1wpadmins
group:mysamlrealm/wpadmins
group:mysamlrealm/wcmauthors
group:mysamlrealm/ldapadmins
group:mysamlrealm/vp3wpadmins
group:mysamlrealm/vp2wpadmins
[7/26/18 15:40:51:721 UTC] 000000bf WSAccessManag 3 reqRoles Security Role [ org.eclipse.jst.j2ee.common.internal.impl.SecurityRoleImpl@f11c8c4b ]
Role Name [ snooprole ]
[7/26/18 15:40:51:721 UTC] 000000bf WSAccessManag < isGrantedAnyRole Exit
true
[7/26/18 15:40:51:721 UTC] 000000bf WSAccessManag < isGrantedAnyRole Exit
true
[7/26/18 15:40:51:721 UTC] 000000bf WSAccessManag < isGrantedAnyRole Exit
true
In the above trace excerpt note the following sections matching the configuration above:
:
Access ID [ group:mysamlrealm/wpadmins ]
:
[7/26/18 15:40:51:721 UTC] 000000bf WSAccessManag < getGroupsIds Exit
group:mysamlrealm/vp1wpadmins
group:mysamlrealm/wpadmins
: